Security in the Tendenci SaaS Cloud at AWS
Cyber Security is based on Prevention, Monitoring, and Incident Response
Associations are part of the fabric of society. We take it seriously. And we also understand there are no "perfect" or "completely secure" systems. Not even air-gapped.
Responsible Reporting
At Tendenci we follow the "responsible reporting" method of disclosure. It is the only ethical one.
https://en.wikipedia.org/wiki/Responsible_disclosure
Please email us at helpdesk [at] tendenci [.] com.
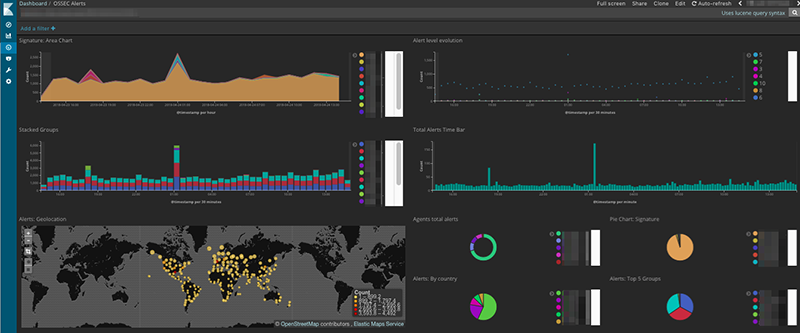
The Current Reality of Cyber Alerts on the Tendenci AWS Cloud
This is what the security alerts on the sites we manage and defend for associations look like.
To guard our SaaS AMS clients' sites we use redundant systems. These include SSL encryption, application isolation, containers, layers of AWS (Amazon Web Services) VPC, Security Groups, ACLs, Route53 DNS, custom AMIs, virus scanners, malware scanners, pen-testing, auditing, and more. All of these activities generate redundant logs which need to be monitored. To do that we run what is called the "ELK Stack" or now the "Elastic Stack".
Read Security in the Tendenci SaaS Cloud at AWS
Cyber Security starts with Project Management
A Cyber PM, upon initial completion, never ends. It requires constant vigilance. The process of Cyber Security can be further explained as:
- Architecture - Start with Security In Mind
- Cyber Security evolves. We start with security and outline the right architecture if it is on-premise or in the cloud.
- Listening - listening is the first step in communication and with cyber security, it is no different. Gathering objectives and identifying everyone involved in the supply chain helps balance economics as well as identify weak links.
- Training - both the client training on their business and our team training them on concepts [discussed in CISSP].
- Plan for a scalable and manageable solution. Technology - like docker containers in AWS, Google, Rackspace, and IBM clouds all provide scalability while maintaining security.
- Patching systems on the fly with minimal downtime
- Processes in place for Change Management
- Consistency of configuration to the extent that it is possible
- Mobile device management
- Encryption
- Passive Cyber Defense - Systems that are in place
- Firewalls (multiple)
- Virus Scanners and malware detection
- Intrusion Prevention Systems
- Intrusion Detection Systems
- File integrity monitoring and reporting
- Active Cyber Defense
- IDS/IPS-controlled dynamic firewalls
- Reporting of IP addresses
- Analyst review of data
- On-going auditing of passive response systems
- Pre-emptive measures (e.b. resetting every user's password without advance notice)
- Cyber Intelligence Gathering
- AI analysis of logs as needed
- Handcrafted Rules specific to a client's environment
- Shadow sites are used to gather information on the attackers (internal or external)
- Honeypot information gathering
- Sharing with the InfoSec community
- Ongoing training for our team and shared with clients as needed
- Response
- Response to a Cyber Attack is a careful art. Once the scope is understood we respond appropriately
- Legal recourse is an option
- We follow all legal requirements of timely disclosure should an event occur
- Crisis Communication rules are DIFFERENT for Cyber Security. Consider your actions carefully.
There are many resources available for cyber security training. We encourage you to look them up and take an active role in keeping your website, company, family, and the country secure from cyber-attacks!
Tendenci - The Open Source will succeed above all. Make no mistake. As long as we keep security our top priority.
Thank You.
We Want to Fully Support Your Organizations Success in the Online World
Your Software. Your Data. Your Choice.
Give us a Call at (281)497-6567